The Dawn of Cryptocurrencies and Blockchain
Whenever a new technology, which is a product of a few previous decades of research and hard work emerges, people from several walks of life may doubt and criticize the revolution that it might cause. But, on the other hand, technology leaders may be astonished and embrace it. Eventually, when it gets commercialized, people may wonder why its potential wasn’t evident in the beginning. Technologies that have gone through this process include Personal Computers in the 1970s, the Internet in the 1990s, and Cryptocurrencies in the 2010s.
Evolution of technology that addresses the drawbacks in digital payments
Money has been a part of human history for several centuries in some form or the other. However, money has seen a massive revolution from the barter system of transactions to the current cryptocurrency system. With the advent of the digital age in the 21st century, money took its digital form, succeeding its previous physical form. Money evolved to a new form to address the problems in its current state and the economy.
There have always been two fundamental problems in any digital payments system.
- Suppose there is no easy way to verify whether an individual had sufficient funds to pay their counterpart in a transaction. In that case, he could engage in double spending – multiple fraudulent transactions – leaving the other unpaid.
- On the other hand, if an individual provided all the required private information to prove that he has sufficient funds, the funds might be stolen before they could be used for the transaction.
The time-tested solution for this problem is the involvement of a trusted third party, which is permitted to have access to the private information of the availability of the funds. This ensured a safe transaction between the two parties without losing funds or information. But these intermediaries charged hefty fees for their service, and it is estimated that the current cost to consumers for cross-border payments is 6.5%.
There is also a problem that these intermediaries can be hacked, compromising vast amounts of private data. A real-life example of this would be the Equifax hack of 2017, where the private details of around 145 million Americans were compromised.
Cryptocurrency and its underlying technology, Blockchain, can address this problem by replacing a centralized trusted authority with a distributed network of users, achieving a decentralized peer-to-peer payment system.
What is a Cryptocurrency?
A cryptocurrency is a digital or virtual currency secured by cryptography, making it nearly impossible to fake or double-spend. Most cryptocurrencies are decentralized networks and are based on blockchain technology—a distributed ledger enforced by a disparate network of computers.
More precisely, cryptocurrencies facilitate payments – or other exchanges of information – between people without the oversight of a central body (like a government or a bank).
So, what is a blockchain, and how does it work?
A blockchain is a distributed database shared among the nodes of a computer network. As a database, a blockchain stores information electronically in digital format.
The primary cryptographic mechanism used in Blockchain is called cryptographic hash function – a mathematical algorithm that creates a mapping from random data to a bit string of fixed size.
Cryptographic hashing is a one-way function, and it is impossible to decrypt. On the other hand, SHA-256 is a popular hash function used in cryptocurrencies, and it creates a digital signature for any input data to a 256-bit hash.
- To illustrate an example of how SHA-256 works, visit http://blockchain.mit.edu/hash/ . Type ‘DATA’, the corresponding hash is ‘c97c29c7a71b392b437ee03fd17f09bb10b75e879466fc0eb757b2c4a78ac938’.
- Even a small change in the data will result in a completely different hash. Example, type ‘DATa’, the resulting hash is ‘09ac1e78592c65b92a29672f6978dee0c8f25a92aded1fb6fbaa8a903bbd7e9e’. However, a given data will always yield the same hash value.
Any given hash can be solved only through the brute-force method, i.e., trial and error. This ensures that one cannot easily recreate the original message from the hash value, and it is also impossible for two different messages to create the same hash value. In addition, this feature enables the network of peers to view the transactions occurring between any two parties.
Each set of new transactions is combined into one block. Data on each block of transactions creates a unique hash or digital signature corresponding to that set of transactions. An additional piece of data included in each block is the hash from the block immediately before it on the chain.
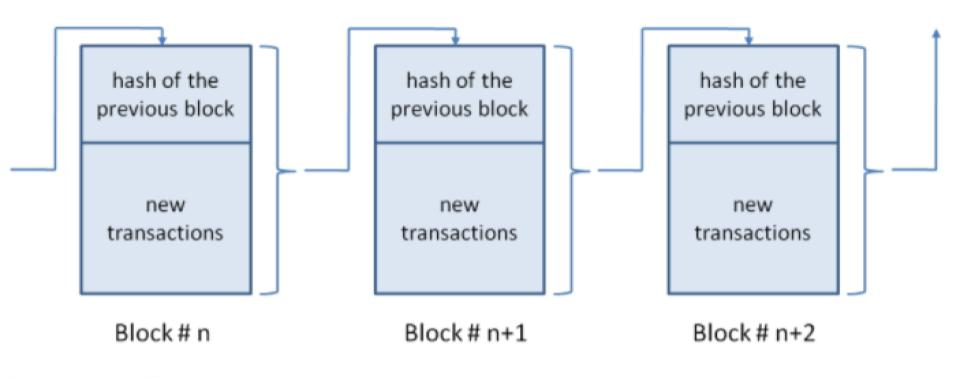
Source: Harvard Business Review
This data structure ensures an irreversible timeline of data when implemented decentralized. Hence, when a node tries to make even the slightest change in the ledger, the hash that the individual generates will not match the other blocks’ hash and, therefore, be discarded. This ensures complete security for the system.
Types of Blockchain systems and their business use cases
Based on their mode of operation, Blockchains are classified as Permissioned and Permissionless. Permissioned Blockchains are distributed ledger systems that are controlled by a central authority. Permissionless Blockchains are not governed by any central authority.
While both permissioned and permissionless Blockchain provides similar value propositions, their mode of control and consensus mechanisms makes one more suitable than the other in specific applications.
Business use case of Permissioned Blockchain systems
- With the application of its IBM Hyperledger Fabric system, IBM worked with Walmart, Kroger, Nestle, and Unilever to ensure food safety.
- The idea behind this initiative was to integrate different parts of the supply chain onto one standard system where each step of the transaction was time-stamped and recorded—for example, isolating food from a farm infected with some virus from the ones produced on shelves. This could potentially reduce food waste and help consumers know more information about the origin of their food.
Business use cases of Permissionless Blockchain systems
- The most popular use case of Permission less Blockchain systems is Cryptocurrencies.
- Ethereum, one of the popular blockchain networks, was the first to develop smart contracts – an algorithm programmed to execute automatically when certain conditions are met – and NFT (Non-Fungible Token) functionality. Moreover, it paved the way to store virtual assets in a decentralized platform, thus making the assets impossible to counterfeit. Popular use cases are digital arts, songs, and even movies held as NFTs.
- Sia – “Decentralized storage for the post cloud world,” as it says on its website, enhances blockchain technology to store files. Zach Hebert, its founder, claims that people need not rely on cloud storage platforms controlled by a central authority in the future. This is because these cloud storage platforms may collapse if their governing authority ceases to exist or stops working due to unforeseen circumstances. Instead, based on consensus mechanisms, these decentralized Blockchains will continue to exist even if the entity that created them ceases to exist.
- CarVertical – This Estonia-based company has deployed blockchain technology to track car histories for people looking to buy used cars. CarVertical captures data on vehicles from various sources, including leasing and insurance history, in one ledger. It then uses the data captured in the ledger to generate a complete report on the car’s history.
- Drife – A ride-sharing app currently operating in Bangalore, India, works through a ‘smart contracts’ system between drivers and riders. Drivers can stake Drife’s native token to be chosen for rides. Instead of paying a commission on every fare, Drife drivers can pay an annual fee to use the app.
Source: techcrunch.com
Operation of Cryptocurrencies on Blockchain
Cryptocurrency is the most popular application of Blockchain. The supply of cryptocurrencies to the market is fixed. They are released by a process called mining, where miners or nodes in the Blockchain network receive them as a reward for approving transactions and adding the transaction details to the Blockchain.
Cryptocurrency mining
Technically, any node in a network can add a new block of transactions. To add a block to the network, the node should solve a complex mathematical puzzle based on a hash function which can be solved only by brute force, and present the evidence of the solution to the other nodes in the network for them to solve it. In reward of this effort, the node that solved the puzzle will be given new cryptocurrencies, and that’s how the market supply of cryptocurrencies increases. This process is known as mining. As a reward for approving the effort, the rest of the nodes get their share of transaction fees. This whole mechanism is called the consensus mechanism.
A consensus mechanism is a fancy way of describing rules that everyone agrees on regarding who updates the ledger. Proof of Work and Proof of Stake are the two most popular consensus mechanisms used in the crypto world.
Proof of work
Proof of Work is a decentralized consensus mechanism that underpins the security of the Blockchain and the legitimacy of the mined blocks to build trust in a decentralized network.
To mine a block, miners solve a complex mathematical problem. The first miner to solve the problem will broadcast his solution to the network, and others can approve his work and earn their share of the transaction fee. In this way, it can be ensured that only the miner who has invested enough work will earn the right to update the Blockchain.
On the flip side, Proof of Work requires a considerable amount of computation power and energy, and it will only increase as the number of nodes in the blockchain increases. Reports suggest mining consumes 132.5 terawatt-hours per year because it is energy-intensive. This has led to miners joining hands to create more powerful computer systems to validate transactions and earn cryptocurrencies, defeating the meaning of decentralization.
Hence, this led to developing an alternative consensus mechanism – Proof of Stake.
Proof of Stake
Proof of Stake states that a miner should keep some coins in stake to mine. Hence the mining power of a miner is determined by the number of coins he puts at stake. It is an alternative consensus algorithm that tries to address the scalability and environmental sustainability concerns surrounding the proof of work (PoW) mechanism.
This process adds some responsibility to the miner to validate the transactions cautiously. This is because he would have placed some of his cryptocurrency at stake, which would be penalized by a slashing process if he validates a bad block of transaction.
Understanding a cryptocurrency transaction
To understand how a cryptocurrency transaction works, we can illustrate a pictorial example of a Bitcoin transaction. Founded in 2009 and touted as the world’s first cryptocurrency, Bitcoin is the most popular and valuable cryptocurrency available today, with a market capitalization of nearly $1 trillion. It runs on the Proof of Work consensus mechanism.
Source: cbinsights.com
Read more about how cryptocurrencies work here.
Conclusion
Cryptocurrency is still in its early stages of development, but it is expected to achieve immense stability over time. This stability makes it a better store of value, making it more reliable and increasing its business application. The Governments and Central banks can leverage this time and regulate it better to harness its potential. Its underlying technology, Blockchain, has already been implemented in several business use cases. Also, with the advent of the Metaverse concept, its future looks promising.